Allakhazam.com: World of Warcraft
Allakhazam.com: World of Warcraft
World of Warcraft site featuring Item Database and other neat stuff.
My blog in the Digital Web. From here you can see the paper trail of what I find on the net that I like, as well as any interesting happenings. Also of interest to some are my writings, small pieces of fiction based on worlds created by others (as is the case of the Exalted sequence), or by me (as in the Dark Ages and Present Time series). My main anchor now is here.
Allakhazam.com: World of Warcraft
World of Warcraft site featuring Item Database and other neat stuff.
Scribbled Here by
Ashtear
at
09:11
0
comments
![]()
Item Set: Vestments of the Devout
My dream equipment in WoW... *sighs*
Scribbled Here by
Ashtear
at
09:10
0
comments
![]()
Bomber for J2ME MIDP 2.0 Compatible Devices
Very nice game for cellphones and such.
Scribbled Here by
Ashtear
at
09:09
0
comments
![]()
Now, this is where my priest is going. Considering my level is 57, I'm almost there.
And this is the build I think I should use for end-game, or when I run out of rested experience.
Any comments, or ideas?
Scribbled Here by
Ashtear
at
02:56
1 comments
![]()
Hello everyone. ^_^
Since I'm now again inmersed into World of Warcraft (WoW), I have decided to add a new section to the links specifically for WoW links. Also, I added some new comics, and fixed a bug in the links for some of my friends.
I also added a game. ^_^
Ash out.
Scribbled Here by
Ashtear
at
02:37
0
comments
![]()
POVCOMP 2004: Welcome!
Very nice visuals...
Scribbled Here by
Ashtear
at
01:57
0
comments
![]()
PukiGame: "
"
Now this is a pretty nifty game
Scribbled Here by
Ashtear
at
01:47
0
comments
![]()
Pasco: Broken TV leads to charges
Now THIS is a woman with cojones.
Scribbled Here by
Ashtear
at
01:43
0
comments
![]()
The only news source you'll never need.
Very funny.
Scribbled Here by
Ashtear
at
00:40
0
comments
![]()
The Great Internet Porn-Off
LOL!!! This is hilarious!!!
Scribbled Here by
Ashtear
at
00:36
0
comments
![]()
Halo 2 and the Criminal Mind
Scary.
Scribbled Here by
Ashtear
at
00:29
0
comments
![]()
A Gamers' Manifesto
Even if you aren't a gamer, give this a read. Very good.
Scribbled Here by
Ashtear
at
00:17
0
comments
![]()
Scribbled Here by
Ashtear
at
04:01
0
comments
![]()
Here we get to see Brian's frustration with Ridge Racer. I echo his sentiments. It's a BITCH!
Nuklear Power - Home of 8-bit Theater: "If I ever find the man who progammed the drone car AI for the EX tour in Ridge Racer for the PSP, I will beat him in the skull with a baseball bat until there's nothing left but a chunky stain.
I will video tape it so I can watch it again and again.
I'll plead innocent at the trial. I'll refuse a lawyer, as one will not be necessary. My testimony will be to give the judge and each member of the jury a PSP and a copy of Ridge Racer.
I expect them to deliberate for less than fifteen minutes and to be a free man later that afternoon.
That many PSPs would be expensive, but it'd be worth it to not only make it legal to kill the fucker who made those cars, but to be the only person who got to do it.
I'd watch that video every night before going to bed. I'd sleep smiling.
"
Scribbled Here by
Ashtear
at
00:32
0
comments
![]()
White Wolf Forums :: View topic - Which Exalted sig characters would you like to see naked?
This is hilarious!!! do check it from the beginning... ^_^
Scribbled Here by
Ashtear
at
08:03
0
comments
![]()
hMM.. i'M SO BORED... i'M HERE AT WORK, THINKING ONA FEW THINGS... i HAVE TO WORK ON THE wHITE wOLF nOVEL coNTEST ENTRY FOR ROUND 2. i STILL HAVEN'T STARTED WRITING ON THAT, AND i'VE NEVER WRITTEN NOTHING CLOSE TO FOUR THOUSAND WORDS BEFORE... i SHOULD GET STARTED ON THAT.
aLSO, i KEEP FINIDING COMICS SHOWING LESBIAN RELATIONSHIPS... MAKES ME WANT TO EXPLORE THAT IN WRITING MORE... i THINK i'LL PLAY WITH THAT IDEA FOR A BIT... ^_^
wISH i KNEW SOME NORMAL LESBIAN FRIENDS WHO COULD HELP ME GRASP THAT. nOT THAT i THINK I'VE DONE BAD ATTEMPTS SO FAR.. *AHEM*
^_^
aSH OUT.
P.S.: I noticed now that I had Caps Lock on while writing this. I WILL NOT retype it. So deal with it.
Scribbled Here by
Ashtear
at
05:40
0
comments
![]()
Chugworth Academy: Updating Monday, Wednesday & Friday.
start from 183... ^_^ That's where I dropped off...
Scribbled Here by
Ashtear
at
05:13
0
comments
![]()
winterotra.jpg (JPEG Image, 400x600 pixels)
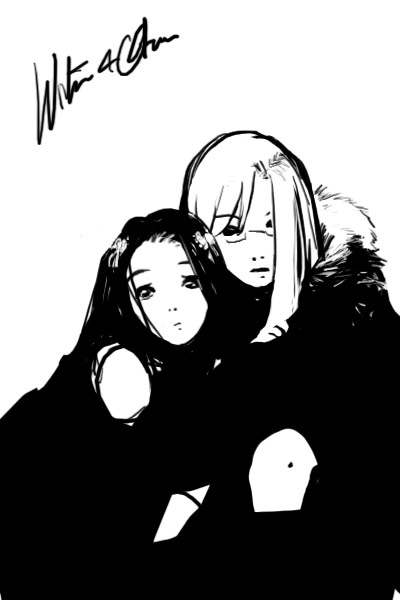
I love this pic so much.... from Clone.Manga
Scribbled Here by
Ashtear
at
03:45
0
comments
![]()
Fire Emblem: The Sacred Stones Media Index for Game Boy Advance at GameSpot
Must download this later.
Scribbled Here by
Ashtear
at
01:37
0
comments
![]()
Jump Super Stars : scans V-Jump
REALLY looking foward to this game...
Scribbled Here by
Ashtear
at
01:36
0
comments
![]()
Scribbled Here by
Ashtear
at
01:26
0
comments
![]()
RPGamer > Final Fantasy XI - Artwork
Pics of FFXI running on the XBox 360. Sweet!!
Scribbled Here by
Ashtear
at
01:19
0
comments
![]()
Final Fantasy XI - Movies
Must download this trailer....
Scribbled Here by
Ashtear
at
01:13
0
comments
![]()
"Because It's an Once in a Lifetime Challenge" Interview with Sony's Ken Kutaragi -- Tech-On!
Interview on the Cell Architecture. Sweet! ^_^
Scribbled Here by
Ashtear
at
01:03
0
comments
![]()
IBM Discloses Cell Based Blade Server Board Prototype -- Tech-On!
Nice, nice. My hopes are really up for this new procesor architecture. Looks promising. ^_^
Scribbled Here by
Ashtear
at
00:44
0
comments
![]()
Airport screeners could see X-rated X-rays | CNET News.com
Now this is scary... It can see through clothing!!! seriously!!
Scribbled Here by
Ashtear
at
00:39
0
comments
![]()
I just had to put this here for safe-keeping. ^_^
Windows Nearly Ready For Desktop Use:
Windows is nearly ready for the desktop, and that includes security as well as LCD driver technology that actually works. This will all happen in the next major revision of Windows, Longtooth.
Sources whom I consider accurate have told me that despite Microsoft's claims that Longtooth will be released by 2006 or 2007, the planned release date is actually late in 2019. Microsoft's secret goals for this version are:
* To reduce the user's perception of the complexity of Windows.
* To gain increased security from emerging threats, such as viruses, worms, spam, spyware, adware, malware, hackers, and phreakers, among others.
Microsoft will accomplish these goals through a variety of changes. First, Longtooth will no longer be based on the Windows NT design philosophy, as were Windows 2000 and XP. Instead, Microsoft will release MS-DOS 9.0 2003, a 64-bit multithreaded DOS written in VisualBASIC.Net, and Windows Longtooth will run on top of that. Also, Longtooth will contain more code changes than any previous version of Windows, both in the number of changed source lines of code (SLOCs) and in the percentage of the total Windows codebase changed. Tremendous numbers of new features are being implemented in completely new code.
More importantly, Microsoft employees are combing through the codebase, in a relentless search for code that is mature, stabilized, and proven. This search has proved difficult, but when found, such code will be marked for reimplementation. I'm told that most of this code will be reimplemented in VisualBASIC.NET, even if the prior version was written in another language, such as C or C++. Programmers making the new VisualBasic.NET code are not allowed to look at the code that already exists, so that fixes to known issues will not be known until well after the software is deployed to millions of users.
The reason for these changes is simple: Study after study conducted by Microsoft has proven that security through obscurity is the only way to go, especially in an operating system deployed to millions of users, with many instances running mission critical applications in finance, industry, government, and other sectors. Microsoft has identified that viruses, worms, spam, spyware, adware, malware, hackers, and phreakers are able to compromise Windows security because vulnerabilities in the code are known. By changing much of the codebase, especially the stablest and most proven parts, Microsoft will thwart the efforts of malicious programmers, as it will take time for them to find the new vulnerabilities in the unknown code.
To meet Microsoft's first goal of reducing the user's perception of the complexity of Windows, Microsoft will integrate a new technology, dubbed Microsoft Windows User Simplicity And Security Manager 2003, into Longtooth. This technology will hide all configuration settings from the user. All settings will be completely automatic, and the user will have no need to know or care what is under the hood. In reality, Longtooth will be the most complex version of Windows yet, with thousands of configuration settings controlling nearly every function of the operating system. The settings will be produced by discovery algorithms designed to automatically set a "sane" configuration. Since there will be no interface to modify any setting, the user will have no choice in his configuration, thus simplifying the user's perception of the system's complexity.
To meet the second goal of increased security, these settings will be scattered throughout the OS, its components, and in other areas of the file system. For example, Microsoft knows that viruses, worms, spam, spyware, adware, malware, hackers, and phreakers are interested in moving the icons on user desktops without the user's permission, so settings controlling the number and size of icons appearing on the desktop will be scattered throughout parts of the registry, batch files, .ini files, web bookmarks, in the Windows kernel, in the file allocation table, in the hard drive's partition table, in hidden tracks on the hard drive, and, if a Linux partition exists, in random areas of this partition, overwriting other data. This manner of storing settings will thwart the efforts of hackers to modify them for malicious purposes. Unfortunately, high security also means a slight reduction in usability. In this case, it will prevent the user's ability to control protected settings like the positions of icons, which is why Longtooth will be fully automatic when it comes to configuration.
On the other hand, Microsoft does not plan to expend unnecessary efforts to protect less important settings. Therefore, unimportant items, such as the user's digital wallet, used to access bank accounts and other private information online, will be stored as cleartext in the file C:\WINDOWS\WALLET.INI. For convenience, users will be able to access their wallet from anywhere over the Internet. For example, if your home computer's IP address is 201.555.193.31, and you want to access your bank accounts from work, all you have to do is connect to http://201.555.193.31/wallet [201.555.193.31], and Windows will supply the file without any troublesome intervention or inconvenient passwords, which users are likely to forget right when they need them most.
Microsoft Windows User Simplicity And Security Manager 2003 includes additional functionality to thwart viruses, worms, spam, spyware, adware, malware, hackers, and phreakers. For example, Windows automatically assumes that any non-Microsoft code might be malicious. It identifies such code by comparing the executable name to a list of Microsoft applications. If the name matches, the code is assumed safe; if the name does not match, the code is assumed unsafe. So, for example, any file named EXPLORER.EXE or NOTEPAD.EXE is known to be Microsoft code and is therefore assumed 100% safe. The OS does not make any safety checks on such code, and the code always runs with full Administrator priviledges. For convenience, this list is stored in C:\WINDOWS\SAFELIST.INI, and can be accessed with read/write permission using any Internet connection.
Longtooth will include a second line of defense against viruses, worms, spam, spyware, adware, malware, hackers, and phreakers. Dubbed Microsoft Malicious Code Stopper 2003, this portion of Longtooth will prevent known malicious code from running. Each time the user attempts to launch a program by clicking its icon, Longtooth will compare the name of the program to names listed in the file C:\WINDOWS\DONTRUN.INI. If the program is listed there, Windows warns the user against running malicious code and prevents the program from starting. When Windows is installed, this file only contains OPERA.EXE and FIREFOX.EXE, two programs known to Microsoft to contain rogue code.
By distinguishing safe Microsoft code from unsafe malicious code as described in the previous paragraph, Microsoft Windows User Simplicity And Security Manager 2003 provides an important layer of security. This security is integrated into the Windows user interface as I described at length in previous posts about Longtooth. A separate line of defense, called Microsoft Longtooth Security Center 2003, will provide an interface to authenticate security events. I will summarize its features here:
User interface features, such as mouse movement and clicks, use of the scroll wheel, keys pressed, menu selections, and other events pass through a special filter when they occur in any part of the interface not controlled by safe Microsoft code. Any time such an event occurs, Windows will display a dialog, asking the user if he is sure he wants to perform that action. The user will have to select "Yes" and enter the administrator password to proceed. This process will be known in Longtooth as "Authenticating an OS event to the user," or simply, as "authentication."
The network layer will be heavily protected. Each network packet received or sent over any interface will require authentication, unless focus is in a Microsoft program at the time, in which case all security checks, including the Microsoft Personal Firewall, if activated, will be completely bypassed. Users will also have to authenticate the loading of any program, unless it is a Microsoft program. Any APIs called will have to be authenticated, unless they are called from a Microsoft program. Any assembly instruction executed in a non-Microsoft program will also have to be authenticated.
By the way, to make sure that a "bot" or some other automated system isn't automatically clicking "yes" and entering the password, and to foil password cracking programs, Microsoft will implement several innovative new technologies. Sometimes, the user will be asked to enter his password backwards. Other times, the password form will request every other character of the password, or every third character, or an ASCII sum of characters located in prime number locations (e.g., the 1st, 2nd, 3rd, 5th, 7th, 11th, etc., characters of the password) in BCD notation, or characters located in Fibonacci number locations (e.g., the 0th, 1st, 1st, 2nd, 3rd, 5th, 8th, etc., characters of the password). In the case of Fibonacci numbers, 0 will refer to the first character, 1 to the second, etc. Longtooth will provide a reference guide and a programmer's calculator to assist the user during this process. Additionally, Windows will sometimes display an image of text that is slightly warped (to foil OCR algorithms that might be present in password crackers) that the user must enter correctly before typing the password.
Again, these authentication checks take place only when running non-Microsoft code. Microsoft understands that so much authentication will make any non-Microsoft program totally unusable for all practical purposes. Instead of getting any work done, the user will spend all of his time entering passwords. Therefore, Microsoft will release what it internally calls a PoK, or "patchwork of kludges," known for marketing purposes as Microsoft Longtooth Password Accelerator 2003. This accelerator will function by capturing authentication events and entering the Administrator password automatically each time, preventing the window from appearing and bothering the user. Since this means the security gained through authentication will be lost, Microsoft Longtooth Password Accelerator 2003 will, at random intervals, disregard authentication events, causing the window to appear. This means that you could be playing Doom III, and suddenly a window appears asking you if you really want to execute MOV EAX,EBX. Or you might have Nero burning a DVD while you're watching TV in the other room, and the burning process will get screwed up in the middle because some window will wait for your password before continuing. These programs will be frozen until you enter the Administrator password. But since Microsoft understands that sometimes you start a process and leave it unattended, Windows will countdown 60 seconds and then simply continue, skipping the action that did not gain authentication. Thus, the unattended program would probably crash or have some other undefined result.
This might seem a bit inconvenient, but high security is more important than proper operation. Microsoft understands that users may be somewhat disappointed when programs crash due to increased security. To compensate, Longtooth will include several innovative features designed to provide an improved user experience.
Clippy, the talking paperclip, along with other Microsoft characters, will appear throughout the user interface to help the user make informed decisions. Dialog boxes and other cumbersome interface elements have been removed in favor of Clippy and his friends. When an authentication window appears, Clippy will be there to make a random choice, if the user doesn't know what to do. In this case, Clippy can flip a virtual coin, which will come with cool animations and sounds. The coin will initially be selected according to the local currency, but the user will be able to choose from over 100 different contemporary and historical coins. Longtooth will also include an optional full-screen animation with cool 3D effects, which can be used during this process or as a screensaver.
Another option is to pit two Microsoft characters, such as Clippy and Einstein, against each other in a variety of games, such as Scissors/Paper/Rock, Chess, Backgammon, Checkers, or Monopoly, with the winning character making the decision. A "best out of three" option will be presented, but better yet, users can combine several of these into a single decision. For example, Clippy and Einstein can play a game of Chess; the winner can play Monopoly with Rover, and the winner of that game gets to flip a 1-oz Krugerrand coin to make the final decision. Thus, the decision process could take a number of hours, and the rest of the computer is frozen during this time for security purposes. Even Ctrl-Alt-Delete will not work during this time.
Hackers or phreakers who gain physical access to the computer during this process might think they are smarter than that: They will push the Reset button, or unplug the computer. But Microsoft has thoughtfully included a journal, similar to a filesystem journal, to protect the system: The next time the system is started, after the system runs Scandisk, Clippy and Einstein will continue their game of Chess right where they left off.
By adding these innovations, Microsoft hopes to make Longtooth fun and inviting, rather than scary and intimidating. This is important to Microsoft, as they are concerned about users who have never used a computer before. These users will find it easier to operate the computer through Clippy, rather than through a scary user interface with icons, buttons, and other confusing elements. Advanced users will appreciate the increased security and peace of mind that Longtooth will bring.
Scribbled Here by
Ashtear
at
00:37
0
comments
![]()
The Official BitTorrent Home Page
Now with a search function...
Wonder how long that'll last...
Scribbled Here by
Ashtear
at
23:48
0
comments
![]()
BitTorrent Files for [Lunar] Anime
Where I get my Bleach from... ^_^
Scribbled Here by
Ashtear
at
17:42
1 comments
![]()
Ok, now, I'm probably gonna get in trouble over this, but I set up on the Music section of the sidebar's links 2 links of interest. Both are radio.blog radios, both with songs from the anime series Bleach. Now, the thing is that I found a way to open their radios in little windows, without having to touch their site. That's why I'll probably get in trouble over it.
In any case, you can do searches from the official RADIO.BLOG.CLUB site for a song, and it'll show you the radios that have that song, so they do even worse than I do...
Oh well... Until I find a way to set up my own, I'll probably be linking to all my favourite radio.blog radios all over the place... *sigh*
Also, all links to radio.blog radios that I set there will have a particular song autoplay on load. To know which song will pop up, put the cursor over the link, and a tolltip should pop up and tell you. The autoload song is probably the song that led me to that radio, so it's usually something I wanted to listen to a lot at that time.
Ash out.
Scribbled Here by
Ashtear
at
06:22
0
comments
![]()
There we go... I added all relevant (and worthy.. HAHAHA!) links that I've collected as individual posts to my links section on the sidebar. Of particular interest is PAPER.HEART's blog.radio, which has some very good japanese music; and a few new entries on the friend's section. Cool people, we'll see how their writing skills on blogs measure up.
^_^
Scribbled Here by
Ashtear
at
04:22
0
comments
![]()
Öz's Dwelling
Another friend's blog. ^_^
Scribbled Here by
Ashtear
at
03:31
0
comments
![]()
hymn -- decrypt iTunes and iPod music / unprotect AAC files (m4p --> m4a): "The purpose of the Hymn Project is to allow you to exercise your fair-use rights under copyright law. The various software provided on this web site allows you to free your iTunes Music Store purchases (protected AAC / .m4p) from their DRM restrictions with no loss of sound quality. These songs can then be played outside of the iTunes environment, even on operating systems not supported by iTunes and on hardware not supported by Apple."
Scribbled Here by
Ashtear
at
02:19
2
comments
![]()
Your iPod just became useful
An iPod management plugin for Winamp. Very good.
Scribbled Here by
Ashtear
at
02:04
0
comments
![]()
Another Leo's Den
Another friend I hadn't talked to in a long time, and who just created his blog today.
Scribbled Here by
Ashtear
at
22:46
0
comments
![]()
Prevenge of the Geek
A college friend's blog. Hadn't known anything of him in a while, so it's cool to see him join the blogsphere... ^_^
Scribbled Here by
Ashtear
at
10:52
0
comments
![]()
Bleach Portal » No Better Bleach Source Than This!
The anime series I'm currently following. Very cool series.
Scribbled Here by
Ashtear
at
07:09
0
comments
![]()
Bathing in the pond's warm waters, I can feel the ancient grove resonate with my soul. Here, in the middle of this forest, stands a small pond of bluish green waters, reflecting the stoic gaze of the many trees that surround it. Here for who knows how long, it probably hasn't seen a living human in a long time. And now, for some reason, I don't know if my heart longs for it's company, or if the pond longs for mine.
Which is why I am not completely surprised when the water before me begins to rise, taking the form of a young human girl, standing in the pond's surface before me. While her form is completely composed of water, she is tinged with the colors of the forest, allowing me to clearly differentiate and appreciate the blue-green eyes, the dark green hair literally flowing down her shoulders, shapely yet firm legs and dark-colored lips, smiling seductively at me.
She lowers herself to grab my hands, and I, lost in the magnificence of the pond's spirit, willingly give myself to her. She lifts me towards her, her breasts brushing my chest, and takes me in an embrace, during which we slowly sink under the water's surface.
I know her like i've never known anyone else, exploring within her form every single nook, cranny, and crevice in the pond, all of them represented in her body. Every curve, every strand of hair, every inch of skin, I explore with my soul, trying to make her as mine as I can, integrating her into the depths of my being. Suddenly the lack of air is of no importance, for I draw sustenance from her essence, my being for this time as diffused into the pond as her love and feelings will allow.
Slowly we sink deeper, to the core of her existence and power. Here we join in a way I never dreamed possible, and that would effectively be impossible because of the limiting aspects of flesh and bone. But these are temporarily circumvented by the power of the pond's spirit. I feel as if I were water as well, and we swirl amongst each other, mingling and completely uniting with each other, true love as it should always be.
Since then, I visit the pond every day of my life. Nothing can keep me away from my love, who always comes to the surface to greet me when I lower myself into her warmth. I have bathed in her hair and drank of her lips, breathed of her flesh while under her skin. She has explored me as well, seeking to know me intimately, and has taken my seed with her, nurturing our love in her womb deep under the waters.
One day I went to the pond, to my love, when I found a baby girl in the waters, breathing of her mother as I breathe the air around me. Her hair is the blue green of her mother's eyes, a slight bluish tint to her skin, yet my eyes and inquisitive nature. She looked at me when I approached the pond, and her mother rose from the waters, holding our child in her arms, and spoke, "Look, my child. Meet your father."
I went to her, the surface of the pond sustaining my weight, and held both her and my child in embrace, tears streaking my face.
My new family, my true family, together.
My mind set, to be with my love and child for the rest of my days, we slowly sank to the depths, never to be seen again.
Scribbled Here by
Ashtear
at
04:07
1 comments
![]()
I wanted to find somewhere to hide
and I opened up and let those fears inside
and I wanted to be anyone else
only to find that there was no one there but me
but I woke up to the real life
and I realized It's not worth running from anymore
when there was nowhere left to hide I found out
that nothings real here but I won't stop now until I find a better part of me
I let those hard days get me down
and all the things I hate got in my way
I could've screamed without a sound
I found myself silenced by those things they say
but I woke up to the real life
and I realized It's not worth running from anymore
when there was nowhere left to hide I found out
that nothings real here but I won't stop now until I find a better part of me thats out there somewhere
and It cant be that far away
thats where I'll find myself
and I'll find my way out
that's where I'll find out
but I woke up to the real life
and I realized It's not worth running from anymore
when there was nowhere left to hide I found out
that nothings real here but I won't stop now until I find a better part of me
Scribbled Here by
Ashtear
at
04:07
0
comments
![]()
3 DOORS DOWN LYRICS
Let Me Go
One more kiss could be the best thing
But one more lie could be the worst
And all these thoughts are never resting
And you're not something I deserve
In my head there's only you now
This world falls on me
In this world there's real and make believe
And this seems real to me
[Chorus]
You love me but you dont know who I am
I'm tore between this life I lead and where I stand
And you love me but you dont know who I am
So let me go
Let me go
I dream ahead to what I hope for
And I turn my back on loving you
How can this love be a good thing
When I know what I'm goin through
In my head there's only you now
This world falls on me
In this world there's real and make believe
And this seems real to me
[Chorus]
You love me but you dont know who I am
I'm tore between this life I lead and where I stand
You love me but you dont know who I am
So let me go
Just Let me goo...
Let me go
And no matter how hard I try
I can't escape these things inside I know
I knowww..
When all the pieces fall apart
You will be the only one who knows
Who knows
[Chorus]
You love me but you dont know who I am
I'm tore between this life I lead and where I stand
And you love me but you dont know Who I am
So let me go
Just let me go
and you me but you dont
you love me but you dont
you love me but you dont know who I am
and you love me but you dont
you love me but you dont
you love me but you dont know me
Scribbled Here by
Ashtear
at
03:40
0
comments
![]()
And such is the current state of affairs that events around your life
force you to disconnect from it as a defensive involuntary reaction,
making you feel disjointed from the events that surround you. Your
destiny detached from the loom of fate that weaves our lives.
That's pretty much how I feel... like i'm not even here...
Scribbled Here by
Ashtear
at
03:07
0
comments
![]()
Waiter Rant
I think something like this is what I miss...
Scribbled Here by
Ashtear
at
02:45
0
comments
![]()
M-Systems 176GB Flash Drive - Engadget - www.engadget.com.
Yowsers!
Don'tunderstand why he struck that out, though... we all know it's true... ^_^
Scribbled Here by
Ashtear
at
02:17
0
comments
![]()
ThinkGeek :: Balloon Lamp
Now this is nice...
Scribbled Here by
Ashtear
at
01:19
0
comments
![]()
ThinkGeek :: Triops Deluxe Kit
An army of facehuggers on my desk... hmm, interesting...
Scribbled Here by
Ashtear
at
01:18
0
comments
![]()
ThinkGeek :: StealthSwitch
Wish I had one of these at work....
Scribbled Here by
Ashtear
at
01:16
0
comments
![]()
ThinkGeek :: Room Defender
This is the sort of stuff I need to keep my brothers off of my room... We'll just load those discs up with some acid or something...
Scribbled Here by
Ashtear
at
01:16
0
comments
![]()
Gee, that was quick.
English bay
Though I don't totally like the shot for some reason... I think it's the angle.
Scribbled Here by
Ashtear
at
00:54
1 comments
![]()
I'd like to take the moment here to point everyone towards Steven's deviantART page. Has some pretty nice pictures, especially this ones:
Sunset at limestone beach I
Sunset at limestone beach II
Winter Berries
Waterfront - Amherstview
So I like sunsets and snow. Sue me!
Hmm, a sunset over a snowy landscape. Wonder how the snow would reflect light at that angle...
Scribbled Here by
Ashtear
at
00:46
1 comments
![]()
Mujeres Vida Blue | Terra
Now this is of particular interest... an interactive Kamasutra... ^_^
Scribbled Here by
Ashtear
at
00:45
0
comments
![]()
: : : : : MapleStory : : : : :
Thanks to Steve (*points at Steve in the audience, who curtly bows*), I finally know what game those pics are for. The game is called Maple's Story, and we have a nice FAQ here, courtesy of IGN FAQs.
Scribbled Here by
Ashtear
at
23:53
0
comments
![]()
Slashdot | Completing BitTorrent Decentralization
Interesting...
Scribbled Here by
Ashtear
at
01:04
0
comments
![]()
Lecturer censored in Spanish University (UPV) for defending P2P networks
Incredible... What lengths man will go to for the sake of their own greed...
Scribbled Here by
Ashtear
at
00:56
0
comments
![]()
ImageShack® - upthejen's gallery
More interesting things on Imageshack
Scribbled Here by
Ashtear
at
03:33
0
comments
![]()
ImageShack® - chelun's gallery
Now Interesting things here.....
Scribbled Here by
Ashtear
at
03:23
0
comments
![]()
